COMMENTS AND REQUEST FOR PUBLIC PROCEEDINGS OF INTERNATIONAL PIPELINE RESILIENCE ORGANIZATION
IPRO finds a critical gap in TSA’s pipeline cybersecurity approach still exists. Without the depth and expertise that comes with administering the Natural Gas Act and the Interstate Commerce Act, TSA may struggle to master the digital and operational complexities of energy pipelines…
IPRO ANALYZES TSA’S PIPELINE CYBERSECURITY REGIME
Today, the International Pipeline Resilience Organization (“IPRO”) called upon the Transportation Security Administration of the U.S. Department of Homeland Security to revamp its framework for ensuring the cybersecurity of oil and natural gas pipelines, whose Informational Technology (“IT”) and Operations Technology (“OT”) remain subject to cyber attack
Collaboration is critical to shield America’s Oil & Gas Pipelines from Cyber Attacks.
IPRO argues that a more collaborative, institutional approach is ultimately the best genuine solution, as opposed to risk mitigation, one incident, one vulnerability, or one standard at a time.
PIPELINE CYBERSECURITY IN THE SHADOW OF THE UKRAINE WAR.
“America Isn’t ready for the Cyber Attacks That Are Coming” NYTimes 3/5 “Russian Hacking Threat Hovers Over U.S. Gas Pipelines” Politico 3/2 “Biden’s infrastructure bill won’t protect your corporation from cyber attack – you’ll have to do that yourself.” The Hill 12/1/21
PIPELINE CYBER INSECURITY AND THE UKRAINE WAR
Oil and natural gas pipeline systems, like the electric power industry, are more vulnerable to cyber attack as the digitalization of their operations have progressed in recent years. Bad actors, including nation-states,…
Biden Official Endorses Effort to Move Pipeline Cybersecurity Regulation to DOE
An emergency directive from the Transportation Security Administration following the Colonial Pipeline attack faced opposition from Senate Republicans after the industry complained they weren’t sufficiently consulted beforehand.
Port of Houston Cyber-Attack--A Reminder of Risks Close to Home!
The operating systems of pipelines in the Houston Ship Channel could have been disrupted and more frequent, more severe attacks are possible in the future, not only at the Port of Houston, but at maritime ports throughout the world.
A Letter From James J. Hoecker our CEO.
In this critical moment, pipeline executives must manage cyber risk more proactively, collaboratively, and with an eye on kinetic wars yet to come. Cyber vulnerabilities are business risks. It’s time to take a fresh look at pipeline cyber protection.
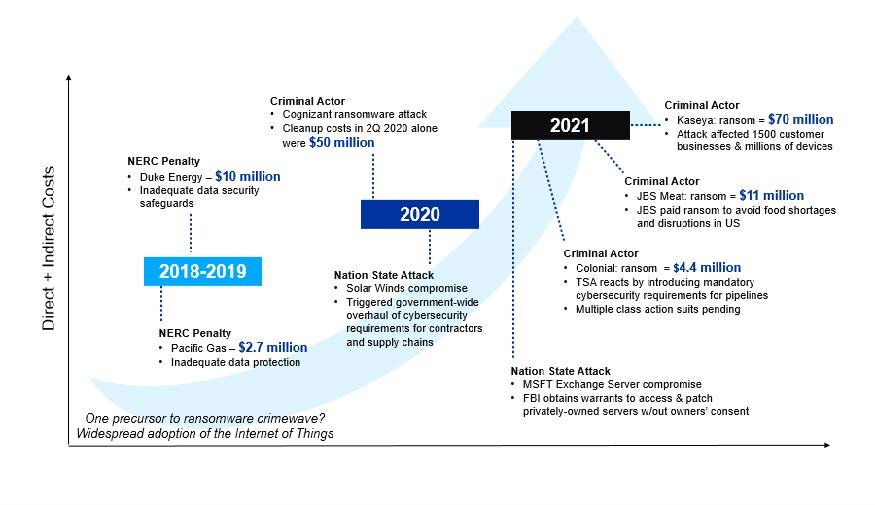
Risk Dominos: Cyber Attack → Operational Failure→ Regulatory Reaction→ Data Exposure→Customer Lawsuit
“During the 1H of 2021, the attacks at Oldsmar, Colonial Pipeline, and JBS Foods demonstrated the fragility of critical infrastructure and manufacturing as it’s exposed to the internet. The attacks showed how attackers could find weaknesses to change chemical levels in public drinking water or use commodity ransomware to shut down fuel and food delivery systems.” (Claroty)
Facing Down the Management Challenges of Cybersecurity
Government agencies have broad enforcement and intelligence capabilities but tend to see things through the lens of national security. Companies have company- or sector-specific risk and operational information. Government and business expose each other to risks and therefore should institute public-private collaboration.
Pipelines Benefit by Uniting Around Pipeline Cybersecurity and IPRO
Security is more than an IT issue and business risk are about more than security. Strong and effective cyber security adds value to the business, and avoids loss of production, ransom demands, loss of reputation, undue delays in recovery, and other business risks. Controlling cyber-risk requires coordination and collaboration with business units throughout the enterprise.
Is The TSA Security Directive A Harbinger Of Oil And Gas Cybersecurity Regulations?
In the weeks that followed a ransomware attack on a domestic pipeline company, the federal government’s efforts to shore up the cybersecurity posture of America’s critical infrastructure and supply chains, including the oil and gas industry, have garnered increased attention.
INDUSTRIAL CONTROL SYSTEM VULNERABILITIES ON DISPLAY
D.C. In its May 26 edition, the Washington Post reported the inevitable. As a consequence of the ransomware attack on Colonial Pipeline and its subsequent shutdown, the Biden Administration and the federal agencies responsible for protecting industry and government from such cyber intrusions are accelerating their plans for new regulations and directives governing the cybersecurity practices of the Nation’s oil and natural gas pipelines. It remains to be seen whether those efforts, which will unfold over many months, will yield benefits to the industry and the public commensurate with the costs.
Statement from FERC Chairman Richard Glick:
“The cyberattack against the Colonial Pipeline system, which provides nearly half of the fuel supply for the East Coast, is a stark reminder that we must do more to ensure the safety of our nation’s energy infrastructure.
Fake News Reaches Risk Management
With all the legitimate concerns about the wildfires in the West, I was dismayed to see that people in Oregon were declining to evacuate because they were convinced that antifa would loot their homes. To try to catch members of antifa, vigilantes even set up roadblocks and demanded that those trying to leave present ID.
INDUSTRIAL CONTROL SYSTEM VULNERABILITIES ON DISPLAY
The shutdown of the Colonial Pipeline in response to an unlawful cyber ransomware attack exposes the fact that, despite the best efforts of several government agencies and the expertise of critical industry sectors, the North American cyber ecosystem remains a dangerous place.